عرض العناصر حسب علامة : Google
الخميس, 16 سبتمبر 2021 10:16
تسويق شركتك: الاستراتيجية الرقمية حتمية
غيّر عام 2020 كل شيء عن كيفية عمل الشركات، بما في ذلك كيفية تفاعلها مع الجميع من الموظفين إلى العملاء ومن البائعين إلى المجتمعات
معلومات إضافية
-
المحتوى بالإنجليزية
Marketing your firm: The digital strategy imperative
By David M. Toth
May 12, 2021, 9:00 a.m. EDT
5 Min Read
Facebook
Twitter
LinkedIn
Email
Show more sharing options
2020 changed everything about how businesses operate, including how they interact with everyone from staff to clients, vendors to communities. The COVID-19 pandemic resulted in a digital transformation that changed the way people purchase consumer products, goods, and services. Until 2020, only 15% of companies prioritized digital transformation. In 2021 however, 77.3% of CIOs rated digital transformation as a top priority, pushing cybersecurity to second place.
Firm leaders of today and tomorrow looking to succeed in an increasingly virtual market must lean into the momentum that has been created since the beginning of the pandemic, take those learning experiences and data points, and uncover new paths to revenue growth.
Digital presence is nothing new and has lived as a function of marketing for a long time. But as client acquisition becomes more complex and anomalies like those of the Paycheck Protection Program and CARES Act have proved to firms that opportunities do exist through virtual experiences, a sound digital strategy must find its place as a pillar of your firm’s 10-year vision.
Empower your firm with the Intuit ecosystem of tax and accounting products
Expand your tax software with tools that help you work better, faster, end-to-end. Intuit offers a full support system, developed by and for tax...
SPONSOR CONTENT FROM INTUIT
The ability to remain competitive in 2021 and beyond is now dependent upon an approach that engages your target audience in tailored and unique ways, either pushing them through a thoughtfully designed qualification process or grooming unqualified leads to become clients of the future. Key tools to a successful plan include:
The evolution of your website into a sales tool;
Leveraging content to answer your audience’s pain points and challenges;
Thought leadership to establish expertise and positioning in key channels;
Comprehension of the “new” client journey;
A tactical approach to keyword strategy and search engine rankings;
Leveraging email marketing that has been a proven tactic in our toolbox for 20-plus years;
Defining the conversion funnel for your firm as it relates to managing each touchpoint;
Identifying digital champions inside your firm; and,
Technology adoption across marketing and sales.
As digital strategy evolves to become an immediate and impactful portion of the client experience, the prospect-to-client journey you create (read: your digital strategy) will require the same level of attention in a virtual environment as it would in-person. The above tools combine to provide rich insight into each visitor’s online movements, interests, and interactions, allowing your firm to curate a personalized, guided experience from the moment they walk in your virtual “front door.”
In fact, prospects and clients already expect and demand a frictionless journey, shifting the traditional focus of business development from relationships in the market to virtual experiences online. Providing a frictionless experience to your prospects and clients requires your firm be able to capture data, automate their interactions, and gain insight from the time they get to your website to the time they interact with your colleagues in the local community. The ability to centralize this information into one dashboard removes the hurdles and unnecessary complexity from a rapidly evolving process.
New opportunities
Geographic boundaries have vanished, but new boundaries related to the virtual buyer’s journey and the pandemic have sprung up between firms and prospective clients. This shift has created a digital strategy imperative. Every facet of the prospect-to-client relationship is now critical to maintaining a data-driven approach to measure what must be managed.
And there are big opportunities to be had. Implementation of a digital rainmaker strategy grants firms the ability to establish meaningful relationships while building a book of business that extends beyond any one individual. Opportunities generated through a broad, sophisticated digital strategy will create an output of higher conversion rates (and more time dedicated to clients and billable hours) for partners, ultimately yielding increased cash flow and profitability for the firm.
So, what are the foundations of a sound digital rainmaker strategy?
1. Data is king. So is content. You may have seen some headlines recently about the way data is going to be collected and stored by internet giants like Google, Facebook, YouTube and Amazon. Their methods are evolving rapidly to put the user first and protect their data. What does that mean for your digital strategy? Data collection will be much more critical at the firm level versus relying on third-party sources. Attention will become a commodity and competition for users’ time on the internet will be more challenging. Strong, relatable content that shows thought leadership will pave the path to establishing an authoritative voice and a strong following.
2. Focus on one vertical at a time. Developing a source of qualified leads through digital marketing of specific verticals and practice lines is the best way to create success stories for repeatable growth. Trying to tackle and embrace the entire firm's transition to one of digital culture will have its challenges. Embracing a model that is generating traceable, repeatable, and sustained revenue comes with focus, leadership, and the ability to identify digital champions within the firm. Who will be the next partner to champion video, thought leadership creation, and a podcast with 40,000 monthly subscribers?
3. Data flow drives decisions. Visibility and accountability at all levels is critical and data flow, analytics, and dashboards connecting the path from marketing inception to sales conversion provide the insight needed to know what’s working and what isn’t. Data-driven growth is integral to the future-ready firm.
4. Adoption at all levels is critical. Why do only 30% of digital transformations succeed? Because, according to McKinsey, adoption must be endemic — and that’s a hard nut to crack. Adoption that starts at the top level and becomes part of the firm's strategic plan, goals, metrics, and key performance indicators at all levels is more likely to succeed and produce the greatest return on investment.
As client acquisition becomes ever more challenging and complex, as client experiences trend toward virtual and away from in-person exclusively, and as the prospect-to-client expectations continue to evolve, this imperative will become ever more critical to your success.
نشر في
موضوعات متنوعة
موسومة تحت
الخميس, 16 سبتمبر 2021 10:08
أمازون والضرائب العالمية
معلومات إضافية
-
المحتوى بالإنجليزية
A U.S.-driven effort to reach a global accord on taxing big tech companies’ overseas profits is getting bogged down over ensnaring one firm in particular: Amazon.com Inc.
A Treasury Department proposal, which was distributed to other governments earlier this month and has been seen by Bloomberg, would subject about 100 of the largest and most profitable companies to greater taxation in countries where the firms’ users and consumers are located, as opposed to the countries where they’re headquartered.
The idea is that the new rules would apply to any large companies that exceed certain numbers, yet to be determined, for their annual revenue and profit margin. Before Treasury Secretary Janet Yellen this month jump-started efforts that the Trump administration had opposed, the talks focused on digital and “consumer-facing” businesses — definitions countries had struggled to reach agreement on.
An employee takes a package from the conveyor belt at an Amazon.com Inc. fulfillment center in Kegworth, U.K.Chris Ratcliffe/Bloomberg
The global talks, led by the Organization for Economic Cooperation and Development, are trying to address many countries’ concerns that tech giants — and other multinationals — aren’t being properly taxed under the current system of rules. The OECD effort seeks to replace the digital services taxes a growing number of countries are enacting to capture more revenue from companies like Google, Facebook and Amazon.
But Amazon’s unusual status as a low-margin tech giant is emerging as a sticking point in negotiations. Seattle-based Amazon recently reported a global operating margin across its businesses of 5.5 percent; that compares with Facebook’s margin of 45.5 percent and 27.5 percent at Google parent Alphabet Inc.
The U.S. proposal called for including only “the largest and most profitable” multinational corporations. It didn’t call for specific numbers, but both revenue and profitability thresholds would have to be set high to capture just 100 companies.
Two Italian government officials, speaking on condition of anonymity, said Amazon should be covered and there’s no reason why a global tax accord can’t capture companies with narrow profit margins but high revenue. Italy, the euro area’s third-biggest economy, has imposed a 3 percent tax on companies with overall revenue above 750 million euros ($903 million) and revenue from digital services in Italy above 5.5 million euros.
A European Commission spokesperson said Tuesday that while the U.S. proposal offers a “promising opportunity” for progress toward a deal, “we should not forget what the initial policy rationale was: a fairer taxation of the digital economy. It is essential that any proposal on the table also addresses this challenge.” A French finance ministry official said they are still examining the U.S. proposal to determine if it would cover all digital multinationals.
The U.S., however, has long opposed an agreement that singles out a particular slice of the economy, such as rules that only affect digital companies, and the new Treasury proposal is intended to make the plan’s scope more quantitative and objective.
U.S. officials are aware that other finance ministries are trying to get low-margin companies captured within the profitability threshold, according to people familiar with the matter, who said Amazon is the target of these discussions. The U.S. continues to oppose efforts to target any single company or sector, said the people, who asked not to be identified.
The U.S. Treasury and Paris-based OECD declined to comment. Amazon didn’t respond to a request for comment.
Not ‘discriminatory’
“We’ve made it very clear to our European counterparts that we will not support a tax that is discriminatory toward American companies,” Wally Adeyemo, the deputy Treasury secretary, said earlier this month on CNBC.
No matter how successful an accord might otherwise be in reshaping tax collection and satisfying calls for multinational firms to pay their fair share to governments, failing to apply it to Amazon — led by the world’s richest person, and a regular target for progressive U.S. lawmakers like Bernie Sanders and Elizabeth Warren over its low tax bill — would risk public opposition to ratification in the U.S. along with European nations.
“Ultimately, it must catch Amazon, otherwise it will be deemed a failure,” and countries might unilaterally introduce their own measures, said Tommaso Faccio, an official at the Independent Commission for the Reform of International Corporate Taxation, a group advocating for overhauling global taxes.
Negotiators are considering the U.S. pitch as nearly 140 countries work to find consensus on both the profit reallocation plan and a global minimum tax, and present it to Group of 20 finance ministers in early July. President Joe Biden recently proposed raising the U.S. minimum tax so the country can collect more revenue from multinational firms and help pay for a $2.25 trillion infrastructure and jobs package.
Business lines
Amazon CEO Jeff Bezos has consistently set low profit targets, preferring to invest in the business, which also reduces the company’s tax obligations. Amazon had 2020 sales of $386 billion, more than Facebook and Google combined, yet it paid less than either company in income taxes. Amazon’s retail business, which includes warehouses around the country and delivery services, costs more to operate than digital advertising businesses run by Google and Facebook.
One method under consideration for including Amazon in the rules would be to allow taxation on specific lines of business, rather than just companies as a whole, according to the people familiar with the matter. For example, if the rules considered the lucrative Amazon Web Services business — with an operating margin of 28 percent — separately from the company’s lower-margin retail arm, countries could still see some of the company’s profits reallocated.
While the U.S. isn’t completely opposed to targeting business lines, it prefers any such practice to be limited, the people said.
In public consultations on previous iterations of the OECD plan, companies have argued that business-line segmentation will become overly complex.
Or, negotiators could also find a different way of setting the revenue and profitability thresholds that does capture the company, Faccio said. That would also risk making the rules more convoluted, after the U.S. proposal sought to simplify what had become an overly complicated determination of which companies would be covered.
“The administration clearly saw the need to inject momentum,” and decided to limit the proposal’s scope in an attempt to get an overall agreement by July, said Alex Cobham, chief executive at the Tax Justice Network. “But the politics will look less smart if the most high-profile companies in terms of public concern about tax abuse turn out to be excluded.”
— With assistance from Spencer Soper, Laura Davison, William Horobin and Nico Grant
نشر في
موضوعات متنوعة
الثلاثاء, 29 يونيو 2021 09:15
بعض أدوات جوجل المجانية التي تساعد العملاء في العثور على شركتك
معلومات إضافية
-
المحتوى بالإنجليزية
These free Google tools will help potential clients find your firm
By Lee Frederiksen
March 12, 2021, 1:12 p.m. EST
In today’s digital world, you can’t make an impact — or remain relevant — if your audience can’t find you. As Google continues to raise the bar for digital marketers and webmasters attempting to uncover the best search terms to attract traffic to their websites, their ability to find the right keywords to draw audiences to their websites has become key to maintaining a pipeline.
Google has made this job all the more difficult by denying access to organic search terms — a change the search engine giant reportedly made to protect individuals’ privacy. Whatever the reason, the result has been a reduction of as much as 90 percent of keyword data available for research. Much of that data is now being represented as “not provided.” Instead of having the luxury of seeing every keyword that drove traffic to their websites, organizations looking to optimize their digital content must now get creative to determine what keywords will work for their online strategies.
Simply stuffing content full of keywords is not a productive optimization strategy either.
Managing Your Firm in a Post-COVID World
Think beyond the pandemic with exclusive resources to help you build a thriving virtual practice.
SPONSORED BY INTUIT ACCOUNTANTS
Search engines, in general, have become a lot smarter. By processing large numbers of queries over time, their algorithms have gotten better at determining searcher intent behind keywords, in particular,whya user is searching. They can then present the most appropriate results, not just offer up “exact-match” search results that may or may not be satisfactory.
Given the rising necessity of proper keywords to achieving greater search engine visibility and the growing number of hurdles to figuring out what keywords will work best to help achieve online marketing goals, any digital marketer worth their salt must be familiar with the tools of the trade. Fortunately, some of the most indispensable tools happen to be free. Let’s take a look at the six best free tools to help you identify the most appropriate keywords for optimizing your content:
Google Auto-Populate: This is the best place to start your keyword research because it reveals what searchers are thinking when they start typing their query. Auto-Populate works by anticipating what searchers are looking for when they start typing and filling in long-tail search terms for them, which searchers often use instead of finishing their own typing. This not only provides clues to popular long-tail search terms but reveals the kind of content that already exists around your topic of interest. Who better to give you suggestions about keyword opportunities than Google?
Google Related Searches: This is another tool that should be at the top of your list when starting your keyword research. Similar to Auto-Populate, this function provides “related searches” at the bottom of most search engine results pages (SERPs). It too reveals popular search terms that Google has already identified and can help you expand your research parameters through word associations.
Google Ads Keyword Planner: This is a good place to start focusing your search for a new keyword. Typing in a prospective keyword will yield data on the average monthly searches for that term, the competition, and a suggested bid price for it, as well as alternative suggested keywords and phrases. You don’t need to be considering a paid campaign to use this function — it’s helpful by showing you alternative keywords you might want to consider and the average monthly searches for the keywords you’re interested in.
Google Search Console: This is the tool for hardcore webmasters and SEO professionals. It reveals the top queries being searched as well as the top web pages returned through search. Search Console will show you both the top queries and the content that has driven the most traffic to your site over the same time period.
Google Trends: Once you’ve established interest in a particular search term, this tool will help you choose the optimal variation of it. You can also use it to compare and analyze the popularity of several variations of your search term over time and even view a forecast for certain terms.
Google Analytics: Just because a large chunk of organic search data is now labeled as “not provided” doesn’t mean Google Analytics can’t be helpful. There is a section under “Acquisition” that contains your Search Console data if you have linked up both platforms. If you look under “Search Console – Queries” you’ll find information similar to what’s in Search Console.
Although it’s become harder to determine what keywords and search terms will work best for your website and other online content, it’s still vital that you do so. It’s also important to remember that all the best keywords in the world won’t help if your content is not useful, valuable and shareable. If the right content is there, visitors will come, and the right keywords will help them find it.
نشر في
موضوعات متنوعة
موسومة تحت
الأحد, 07 فبراير 2021 12:49
هل بيانات شركتك آمنة؟
معلومات إضافية
-
المحتوى بالإنجليزية
Is your firm's data safe?
By Ted Needleman
January 29, 2021, 9:00 a.m. EST
11 Min Read
Facebook
Twitter
LinkedIn
Email
Show more sharing options
It seems like not a day goes by without news of networks being breached and data hacked. One of the most recent, the SolarWinds hack, led to breaches within multiple areas of our government, while individual ransomware attacks on vital parts of our economy, including entire towns and hospitals, are being reported more and more frequently.
Given the chaos that the COVID-19 pandemic has caused through 2020, and with no quick resolution in sight, the last thing you need is for your practice to be hacked or held for ransom. But the plain truth of the matter is that the need to work remotely, fueled by the coronavirus, has made your practice and your clients more vulnerable than they were in the past.
“The rash of lucrative ransomware attacks over the past year pointed to organized hacker groups specifically targeting medical, legal and accounting businesses where they could not only invoke the ransom but also steal a treasure trove of client/business information,” said Roman Kepczyk, director of firm technology strategy at Right Networks. “This allowed the hackers to threaten to release confidential client information or intellectual property if the ransom was not paid. In addition to using the personally identifiable information to fraudulently file tax returns and instigate identity theft, in some instances the hackers contacted clients of the firms for further extortion, threatening to release confidential, compromising or embarrassing information.”
Article Managing Cash Flow– a Critical Factor to Small Business Success
Your small business clients are a key pillar of the U.S. economy, providing income to their families and delivering growth and innovation to the...
PARTNER INSIGHTS
SPONSOR CONTENT FROM CHASE INK
Obviously, protecting your systems and data from outside intrusion is important. But even more important is protecting your clients’ systems and data. And the fact that many of us are working from home, and will likely continue to do so, at least part-time, for the foreseeable future, only increases the risk of exposure.
The steps you can take range from very basic to ultra-sophisticated. Your first lines of defense are great backup procedures and using a good anti-malware application. But these are just the beginning. You need to take active measures to protect your systems, whether they are in your physical office, or your office on the kitchen table.
It takes two
Two of the most common and easiest security measures to implement are two-factor authentication and encryption. While two-factor authentication can be a bit annoying, having to enter both a password and a verification code sent to an email account or messaged to a mobile account significantly reduces the chances of a breach if someone is able to get hold of your password.
Stronger passwords with greater security are also a must. Too many are still using weak passwords such as the names of their spouses, children or dogs, or even “Password123.” Many remote applications are now insisting on stronger passwords containing upper- and lower-case letters, numbers and special symbols. But keeping track of these, especially when they are different for every application, is a major concern for many users. If this is the case with your practice, there are several ways you can use difficult-to-guess passwords and still not have to write them down to remember what they are for each application.
The most common of these is to use a password manager that tracks your passwords and inserts the proper difficult-to-remember password into the appropriate application. Popular password managers include 1Password and LastPass, but there are plenty of similar applications for PCs, Macs, smartphones and tablets.
Another alternative is to use a hardware authentication key that plugs into a USB-A oe USB-C port or provides NFC (near field connectivity — the technology used in tap-and-pay credit cards and some phones) to work with mobile devices that incorporate this feature. One popular key is offered by Yubico, though they are far from the only vendor.
“The YubiKey provides users with a hardware-backed strong multifactor authentication solution that has a proven track record for protecting accounts,” Chad Thunberg, chief information security officer at Yubico, told us. “Not every service provider or application — including some of the popular accounting software suites — have yet adopted the FIDO [Fast IDentity Online] authentication standards that we use for the YubiKey. However, many of these applications support using a single sign-on [SSO] identity provider that does support the use of YubiKeys. To get started, users can enroll their YubiKey with their favorite identity provider (e.g., Google, Apple or Microsoft) and then use that identity provider to log onto their accounting software. I took a brief look at some of the popular offerings, and FreshBooks, QuickBooks Online and Sage Accounting all support SSO.”
Encryption is yet another option that you should be aware of. Richard Kanadjian, encrypted USB business manager at Kingston Technology, pointed out that, “Encryption basically means that if you encrypt the data on that USB drive and you lose it, the probability that somebody can actually retrieve that data is actually infinitesimal. It’s actually almost zero. And the reason is we have password controls. For example, you have a password or a pin for your USB drive and our encrypted drive will only let you enter the password 10 times. So, if you enter it more times and if somebody’s guessing, the drive will literally wipe its contents and erase the data. You will actually not have any data to be exposed to a breach.”
Keeping the data for your applications on an encrypted drive is a usable approach, but keep in mind that the data on an encrypted drive should be backed up to a secure location, be it the cloud or a second encrypted drive, just in case the encrypted drive containing important data is lost or stolen.
You should also be very aware of where you are using your laptop. Too many people go down to the local coffee shop or library, where the internet is freely available, and don’t take reasonable precautions against infections and intrusions. Infecting the routers at these locations with malware is becoming very common, and the compromised internet at these locations can infect hundreds or even thousands of the systems being used there, as well as any networks that the infected systems are then attached to.
“One of the biggest concerns that we are seeing is so many employees were forced to work from home and all of a sudden they’re sitting on networks that are outside of the control of corporate IT,” Stephen Lawton, special projects editorial director at SC Media, pointed out. “If you let the employee simply use their home systems and their home networks without any IP control, quite frankly what you’re going to get is BYOD — not ‘Bring your own device,’ but ‘Bring your own disaster.’ The lack of security controls on most home networks is really quite astounding. Many people have never updated the firmware and their routers. They’ve never put any kind of security controls or software on their systems. If you’re going to have your workers working from home, the practice really needs to invest in laptops specifically for that purpose, that have security controls built into them. At the minimum you need some enterprise-class antivirus, anti-malware anti-ransomware software. You should also have the systems going over a virtual private network back to a home base. VPNs are certainly not foolproof, but they’re better than not having anything at all, or just going through the employee’s personal network.”
© Pedro Nunes/pn_photo - stock.adobe.com
Your face and your printer
Biometrics as a password substitute are also becoming increasingly common. No, you don’t have to have a retina scanner mounted on your PC or laptop, though it would hardly be surprising to see something along those lines using the almost-ubiquitous webcam in the near future. But while retinal scanners have been around for years, along with the handprint readers often seen in movies, they are pretty much relegated to very high security installations with equally high security budgets and resources.
But real, usable, biometric roadblocks to unauthorized network and device penetration have been available for years. Fingerprint readers, especially in laptops, are common these days. And both the iOS and Windows operating systems have facial recognition capabilities that can not only serve as an alternative to system passwords, but in many cases can also be used as passwords to sensitive applications such as bank and credit card accounts.
This is a handy inroad to your sensitive systems and applications, but is somewhat blunted by the fact that most of the facial recognition capabilities at the entry level, such as those included in the operating system, require that the entire face be visible to provide authentication. Wearing a mask, a necessity out in public or in your office these days, often defeats this handy sign-in method.
One area of vulnerability that’s been getting more attention recently are devices connected to the Internet of Things — components, such as printers and multifunction printers, that are connected to your network and also have their own pathways into the internet. Most of us are familiar with threats such as phishing and embedded malware, but there is another route into your network that you may have not considered.
“A lot of times the network perimeter has, in the past, been used as a way to secure devices.” Shivaun Albright, chief technologist of print security at HP, pointed out. “And in this day and age, with email, phishing attacks, clicking on something, any type of email or link, you cannot guarantee that your interior perimeter network is secured. You just can’t. And one of the things that we’ve seen, in fact last year, was an article from Microsoft in August of 2019. They had highlighted that they had caught Russian state hackers using IoT’s breached networks. And, by the way, they found that devices that had been hacked were Voice over IP phones and office printers.”
Clients are targets, too
There’s obviously a lot more to look at security-wise than what is covered here. And, as with many aspects of technology, IT security is a moving target — what’s true and secure today might be vulnerable tomorrow. Developing the expertise and knowledge to deal with the new threats that emerge every day is not only an ongoing process, but one that can be difficult to maintain and expand, which is yet another good reason to examine the practices and protocols in place in your practice and at your clients’.
Protecting your and your clients’ data is not only a fiduciary responsibility, it’s also good business practice. “Firms that have been breached will not only have to deal with a damaged reputation, but can expect to see client churn and having to deal with ongoing litigation from clients that were impacted,” warned Kepczyk.
It takes time and money to build expertise in this area. And even after an extensive immersion in security, it’s likely that you still might not have the experience to know just how to determine where your practice’s vulnerabilities are and how to address them when you do discover them.
One approach suggested by Randy Johnston, executive vice president of K2 Enterprises, that is especially applicable if you outsource some or all of your IT support, is to “choose reputable IT providers that understand and implement best practices for security to help your internal IT staff. While security risks morph over time, the provider must actively respond to new threats and continuously adjust their security protocols and technical setup to protect your firm.”
And Kepczyk added, “Employee training is critical, particularly in regards to phishing threats, which account for the entry of the vast majority of breaches, so we suggest you outsource that to third parties such as KnowBe4, PhishMe, Wombat Security, etc., that will do phishing testing and employee training.”
If you’re thinking of expanding your practice into this growing area of concern, or just want to better educate yourself, Jim Bourke, a partner and managing director of advisory services at Top 100 Firm WithumSmith+Brown, has a few suggestions on getting started. To start, “I would highly recommend getting your hands on the AICPA cybersecurity risk management reporting framework.”
Bourke added, “I would discuss the AICPA’s ‘SOC for Cybersecurity’ engagement with your clients. At Withum, we are all over that space. As CPAs, only we can issue a ‘SOC for Cybersecurity’ report! There is huge demand for this type of deliverable today. The AICPA has classes and workshops in this space, allowing any CPA to gain the knowledge and expertise that they need to perform these services.”
But whether or not you decide to add security consulting to your practice or partner with a company that has expertise and reputation in that area, keep in mind that the very last thing you want to tell a client is that you had a data breach, were hacked, or that your system is locked due to ransomware. A good backup strategy is a necessary first step, but where you go from there is going to determine just how secure your ongoing livelihood is going to be. And while there is no such thing as perfect security, you need to be aware of where you are vulnerable, and take steps to strengthen those areas of your procedures and practices.
نشر في
تكنولوجيا المعلومات
موسومة تحت
الأربعاء, 21 سبتمبر 2022 11:40
كيفية جمع المستندات من العملاء أثناء العمل عن بُعد؟
مع عمل الكثير منا من المنزل بسبب فيروس كورونا ، فإن الطريقة التي نعمل بها مع العملاء بأكبر قدر ممكن من الكفاءة أصبحت أكثر أهمية من أي وقت مضى
معلومات إضافية
-
المحتوى بالإنجليزية
How to collect documents from clients while working remotely
PRACTICE MANAGEMENT, WORKFLOW TOOLS
April 23, 2020 / Mariette Martinez, EA
With the tax deadline postponed and many of us working from home due to the coronavirus, being as efficient as possible with the way we work with clients is more important than ever. To be successful, we need to move more clients online. This starts with operating a 100 percent cloud-based practice and implementing an effective process for document collection.
Since my clients’ technical skills varied from highly tech savvy to new online app users, it was essential that the technology and client implementation would be seamless and user friendly for my multiple client types. I also wanted to keep our workflow as simple as possible, so using the fewest number of applications would create the best-case scenario. I wanted to synchronize what I had already implemented in my current operational workflow, while partnering that with serving my clients’ needs to stay connected. Ultimately, these processes provide me the necessary documents to keep our work flowing seamlessly.
I know that making these kinds of changes in your practice isn’t easy – and it takes time, especially now that we’re sheltering in place. According to an Intuit® Accountant Panel survey in March 2020 that asked about the most pressing issues due to the coronavirus, 42 percent of the 247 respondents said that getting documents from their clients was by far their biggest struggle when working virtually.
Whether you’re very experienced in collecting documents from your clients without seeing them in person – or if this is new for you because of the coronavirus, here are several best practices I can share to make the process easier.
The essence of a strong document collection platform, also referred to as a document portal, is a centralized, secure location to share documents and collaborate with clients and staff.
We chose Citrix ShareFile for our preferred solution, but several other options include Box, Dropbox, Google Drive, SmartVault and Intuit Link.
Several platforms allow firms to personalize the document portal experience with their firm branding to provide a more trusted and professional client experience. These document platforms also commonly enable:
Collaborating on documents and editing in real time.
Encrypted client requests with notifications and reminders.
Encrypted email for those times when email is the best way.
Sending and receiving of large files.
Most importantly, the document collection solution you choose should include a high level of encryption for your files, large space storage capabilities that can scale with your firm, and online and desktop automated syncing of all stored files. You definitely don’t want to encourage clients to send you their documents over email. The bottom line is that you and your clients should be able to securely share, collect, and collaborate on documents no matter where you are.
In addition, several platforms integrate with other helpful tools. One of my favorite integrations is Slack with Google Drive. What are some of your favorite integrations? Leave a comment below to share your recommendations.
One other concern: What do you do if your clients don’t want to send you their documents through the cloud? These “shoebox” clients may not be tech savvy and prefer physically dropping off their information to you, but if you’re working remotely and cannot see them in person, what do you do? You don’t want to lose a long-term client, so here are several recommendations:
Sit down with them over a phone conversation, or if they can figure it out, a web call, to explain how your portal works. Walk them slowly through the process and perhaps have them practice or test uploading something to you.
Record a quick video that also explains the process and send this to your clients who may need help using the platform. You can also include a link to the video in your email signature. Here’s an example of this type of video.
If a client absolutely insists on dropping off or mailing their documents, the best advice I can give is to go with the flow, and ensure your clients have a secure, private place to leave their documents with you outside your place of work to avoid contact during drop off. Most likely, this will be a very small slice of your client base.
When you find and implement the winning platform, you not only stay safe during this time of social distancing, but you will save time on document collection in your practice and witness the magic of productive collaboration. Good luck!
نشر في
موضوعات متنوعة
الخميس, 31 ديسمبر 2020 12:41
أسوأ كلمات المرور لعام 2020، وقصص تقنية ربما فاتتك!
نشر في
تكنولوجيا المعلومات
موسومة تحت
الإثنين, 30 نوفمبر 2020 14:44
ثلاث طرق لإدارة الفرق البعيدة بشكل فعال
نشر في
موضوعات متنوعة
موسومة تحت
الإثنين, 17 أغسطس 2020 14:38
اختبار الأمان عن بُعد
نشر في
تكنولوجيا المعلومات
الإثنين, 23 مايو 2022 14:25
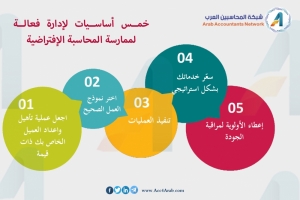
إنفوجرافيك..خمس أساسيات لإدارة فعالة لممارسة المحاسبة الإفتراضية
نشر في
إنفوجرافيك
موسومة تحت
الخميس, 22 سبتمبر 2022 08:10
خمس أساسيات لإدارة فعالة لممارسة المحاسبة الإفتراضية
نشر في
تكنولوجيا المعلومات